Stay always Up-To-Date!
Read our white papers and e-books and find out what is up in IT-Security world! All posts are based on knowledge of our engineers and partners.

Zero Trust at Glance! Explore the benefits!
Zero Trust Exchange is a modern approach that enables fast, secure connections and allows your employees to work from anywhere, using the internet as the corporate network. Read this white paper and find out even more!

Whitepaper: Security, User Experience & Hybrid Workforce's Productivity
Security meets User Experience: Read this whitepaper and dive deeper into the possibilities of how you can enhance the productivity of your hybrid workforce.

Fix-It Guide
This overview about Zscaler Internet Exposure Analysis helps you to fix any open security gaps and offer additional recommendations. Read and find out more.

Zero Trust Architecture Against Ransomware.
Here are 10 ways in which Zero Trust architecture can help your organization defend against ransomware. Check this e-book now and find out more!

Solution Brief: Zscaler Private Access (ZPA)
ZPA is the world’s most deployed ZTNA platform, applying the principles of least privilege to give users secure, direct connectivity to private applications running on-prem or in the public cloud while eliminating unauthorized access and lateral movement. Check out this solution brief and find out more!

E-Book: Why Network Monitoring Tools Fail?
There is a fundamental shift happening through secure digital transformation, which includes application transformation (data center to SaaS, IaaS, PaaS), network transformation (hub-and-spoke to direct connectivity), and security transformation (castle-and-moat to zero trust). Read and find out more!

An Architect's Guide to the Zscaler Zero Trust Exchange
Network and security professionals overseeing zero trust initiatives should read this guide to learn how to deliver effective control and visibility across their Zero Trust initiatives.

Phishing Report 2023
This report will help you recognize the social engineering tactics and sophisticated coding used in phishing attacks, so you can prevent costly data breaches. Read on for an in-depth look at the latest phishing trends and observations.

Zero Trust adoption is on the rise…
Here’s a diagnostic guide outlining seven symptoms that your firewall is unfit for today’s zero trust security world. Any one of these seven symptoms is a sign that your organization needs a cloud security cure.

E-Book: Transformation Through Zero Trust
As the internet becomes your new corporate network, zero trust provides the path to fast, seamless, and secure access across your entire business ecosystem. Explore the countless benefits of a true zero trust platform.

E-Book: Enabling the Modern Workplace - with the Zscaler Zero Trust Exchange.
Modern workplace enablement, secured. Empower your workforce and your business ecosystem with the Zscaler Zero Trust Exchange.

White Paper: Work-from-Anywhere
The enterprise must be able to prevent the risk of exposure while still allowing their employees to access the internet and applications needed to stay productive. But how?
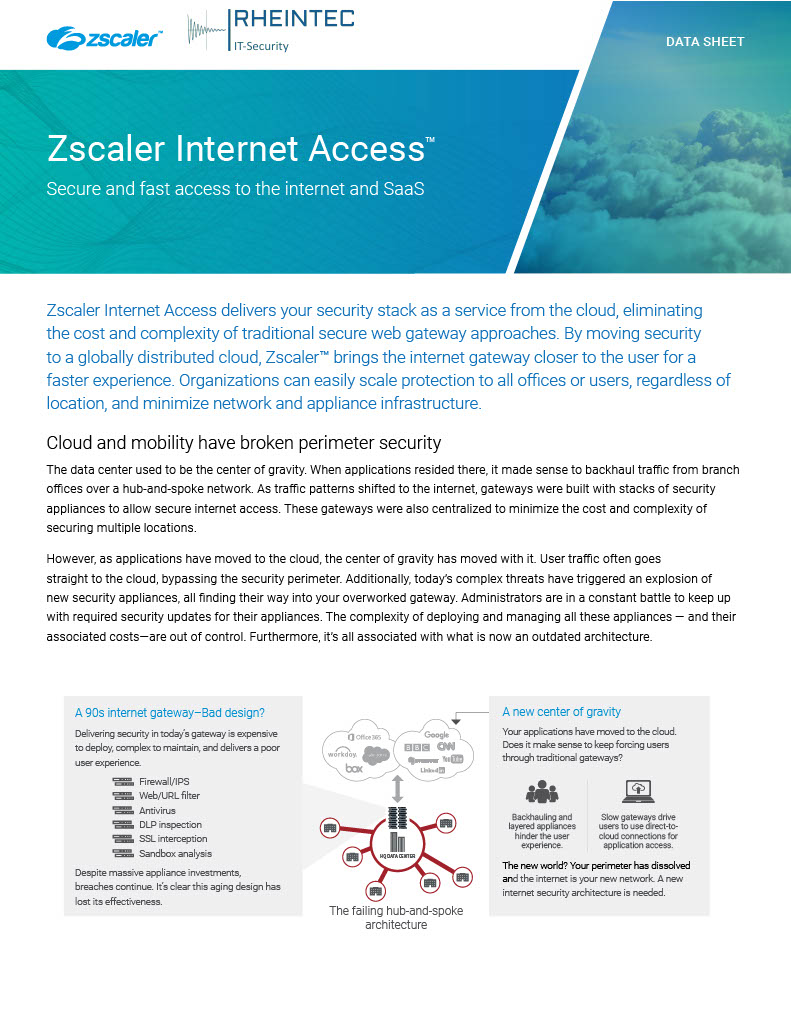
Data Sheet: Zscaler Internet Access
Zscaler Internet Access sits between your users and the internet, inspecting every byte of traffic inline across multiple security techniques, even within SSL. You get full protection from web and internet threats. And with a cloud platform that supports Cloud Firewall, Cloud IPS, Cloud Sandbox, Cloud DLP, CASB and Cloud Browser Isolation, you can start with the services you need today and activate others as your needs grow. Read this Data Sheet and find out more!
If you could improve something about your IT security, what would it be?
Contact us!
Want to get in touch? We’d love to hear from you.
"*" indicates required fields